About Us
Securing Digital Assets is Simple with IT on Cloud.
At IT on Cloud, we specialize in providing top-tier cybersecurity solutions tailored to meet the needs of businesses in an ever-evolving digital landscape.
16
+
Years of Experience
With over 16 years of industry expertise, we have been helping organizations secure their digital presence.
200
+
Protected Servers
We have successfully secured over 200 servers, ensuring robust protection against cyber threats.

Our Partners
Empowering Businesses Globally with Trusted Partners





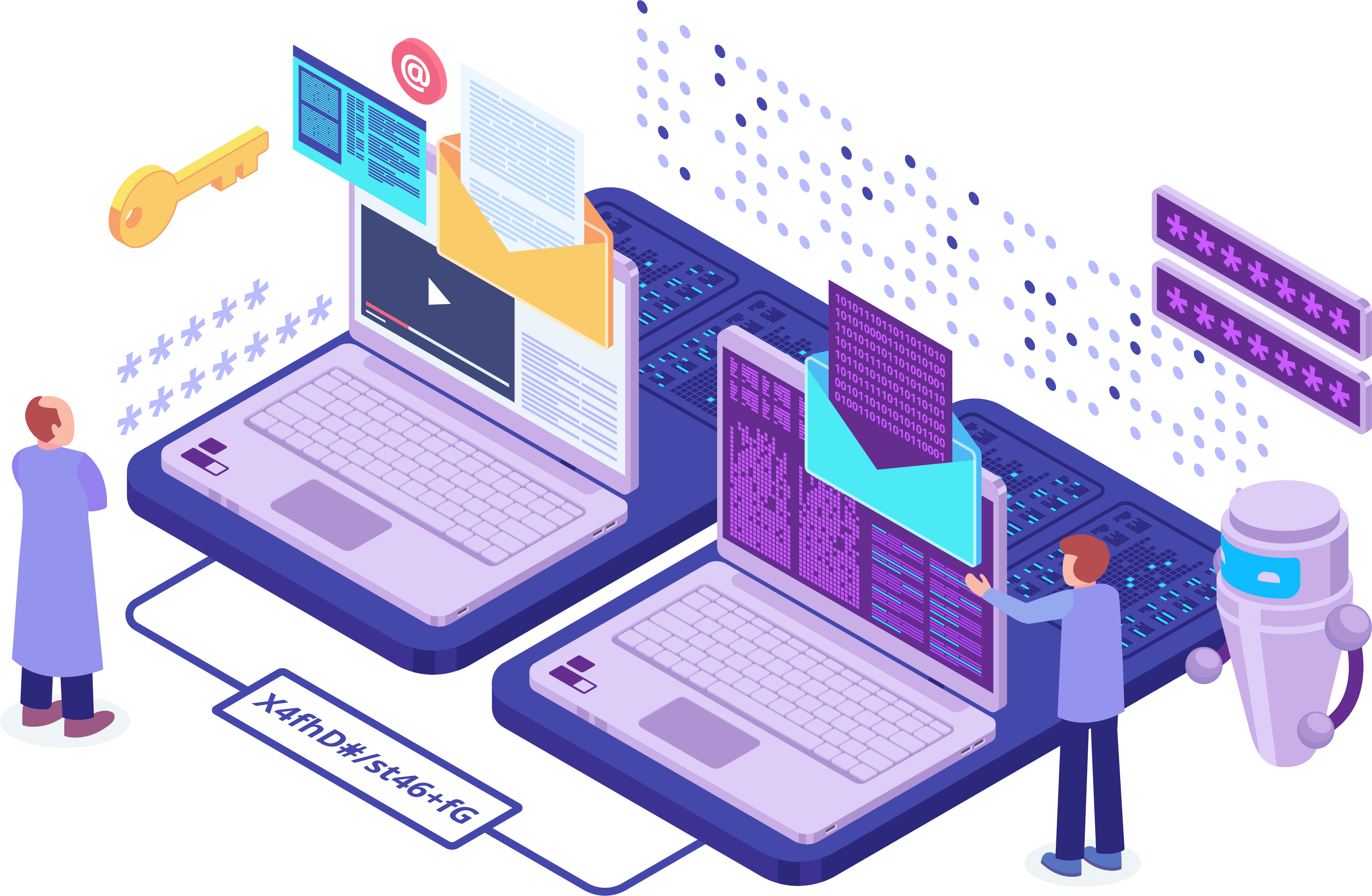
Why Choose IT on Cloud
Reliable Protection for Your Digital Presence
At IT on Cloud, we provide cutting-edge solutions to safeguard your online platforms against evolving cyber threats.
Learn More

Network Traffic Analytics
Gain insights into your network’s performance and identify potential risks with advanced analytics tools.

Enterprise-Proven Threat Detection
Protect your business with our proven solutions designed to detect and mitigate enterprise-level threats.

Cybercrime and Fraud Detection
Stay ahead of cybercriminals with our robust tools for fraud prevention and real-time detection.
Our Services
Empower Your Digital Space with Cybersecurity Solutions
At iTimes Solution, we offer innovative and reliable services to ensure the safety and privacy of your digital assets.

Data Center & Virtualization
Optimize your server performance and protect your systems against potential threats with our state-of-the-art virtualization solutions.

Video Surveillance
Enhance your security infrastructure with our advanced video surveillance solutions to monitor and protect critical areas.



View All Services

How We Work
Empowering Businesses with Technology
At IT on Cloud, we specialize in delivering customized IT solutions to address your business challenges effectively and securely.
01
Understanding Your Needs
We begin with a detailed analysis of your business objectives and challenges to craft tailored solutions.
02
Developing Smart Solutions
Our team designs and develops cutting-edge strategies to streamline your processes and ensure scalability.
03
Implementing Success
We integrate our solutions seamlessly into your operations and provide ongoing support to maximize results.

Testimonials
You choose, we protect
Our customers trust us to safeguard their digital worlds. Here's what they have to say.
Blogs
A better way to do digital.

How to Secure Your Mobile Application's Source Code
Learn how to secure your mobile app’s source code to prevent unauthorized access and protect sensitive data.
Learn more
Addressing Encryption Vulnerabilities in MD5 and Plain Text
Explore the risks of using MD5 and plain text encryption and why stronger encryption methods are necessary.
Learn more
Cyber Criminals and the Risk of Stolen SEP Data
Understand the growing threat of cyber criminals exploiting stolen SEP data and how to protect against it.
Learn more










